
Secure Information Handling
All users are responsible for safeguarding and monitoring sensitive data against unauthorized disclosure, modification, and destruction. Sensitive data may be used only for KCTCS related business in accordance with its policies and standards. A wide variety of third parties have entrusted their sensitive data to KCTCS for business purposes, and all employees should safeguard the privacy and security of this information.
KCTCS ensures that sensitive data is properly handled, whether being transmitted within the organization or to a trusted external third party. This document provides guidance on how to handle sensitive data, including the physical security requirements and the distribution of sensitive data internally and externally.
KCTCS Login Security Measures
KCTCS enforces two-factor (Multifactor Authentication) for all Faculty/Students/Staff. This ensures the user requires at least two forms/factors of identification to logon with their KCTCS userid. This applies to both local PC logons and web based logons.
WIFI Security measures
KCTCS discourages the use of non-sanctioned, public WIFI using KCTCS owned devices. While on campus, KCTCS promotes the Student-Guest WIFI which is sanctioned and has more security controls built-in to its design to prevent malware and other unwanted threats from targeting your machine. With this in mind, it is still best to perform all personal banking and ecommerce purchases at your home residence and not on site at a KCTCS campus.
WIFI access at Coffee Shops, Hotel Rooms, and other free WIFI access points are not to be trusted without the use of a VPN. KCTCS has no visibility into these WIFI access points and cannot ensure their protection.
Secure Web Browsing
Allows make sure when browsing the web to check for a site certificate in use on the website in question. It generally resembles a lock in the URL bar at the top of your web browser.
DLP and Safeguards - What is DLP?
Data loss prevention (DLP) helps to reduce the risk of users sending sensitive or critical information both within and outside the KCTCS network. The term describes a solution that helps security and enterprise administrators safeguard the data that users can transfer. DLP products use business rules to classify and protect confidential and critical information so that users cannot accidentally or maliciously share data, which would put the organization at risk.
Properly Handling Sensitive Data
There are several secure options of handling sensitive data with respect to those who have a business need and on a need-to-know basis. The general breakdown is as follows.
- You should always use the KCTCS institution email address to communicate with students
from your official institution email account
- The employee/student can be subject to data loss via a third-party data breach when using personal email for sending and receiving sensitive information. In the best interest of the employee/student, KCTCS requests that you never send sensitive content to a student’s personal email address.
- Emails should be limited to communication between the school official and the individual student, or between school officials with a ‘legitimate educational interest’ in the student about whom the email is concerned.
- No information about a particular student should be included in an email sent to all members of a class or organization in which that student participates.
Securing sensitive content via Microsoft Teams
Teams is our first recommendation. Any file sent via Teams chat is automatically shared out via the sending user’s OneDrive and would be a more efficient and preferred means of sending sensitive information. This makes it so one does not have to construct sharing links and a follow up email to share your sensitive information. Files sent in this way over Teams chat go to Microsoft Teams Chat Files in the sending user’s OneDrive with permissions for just those in the chat or group chat, which can be revoked at any time, as seen below:
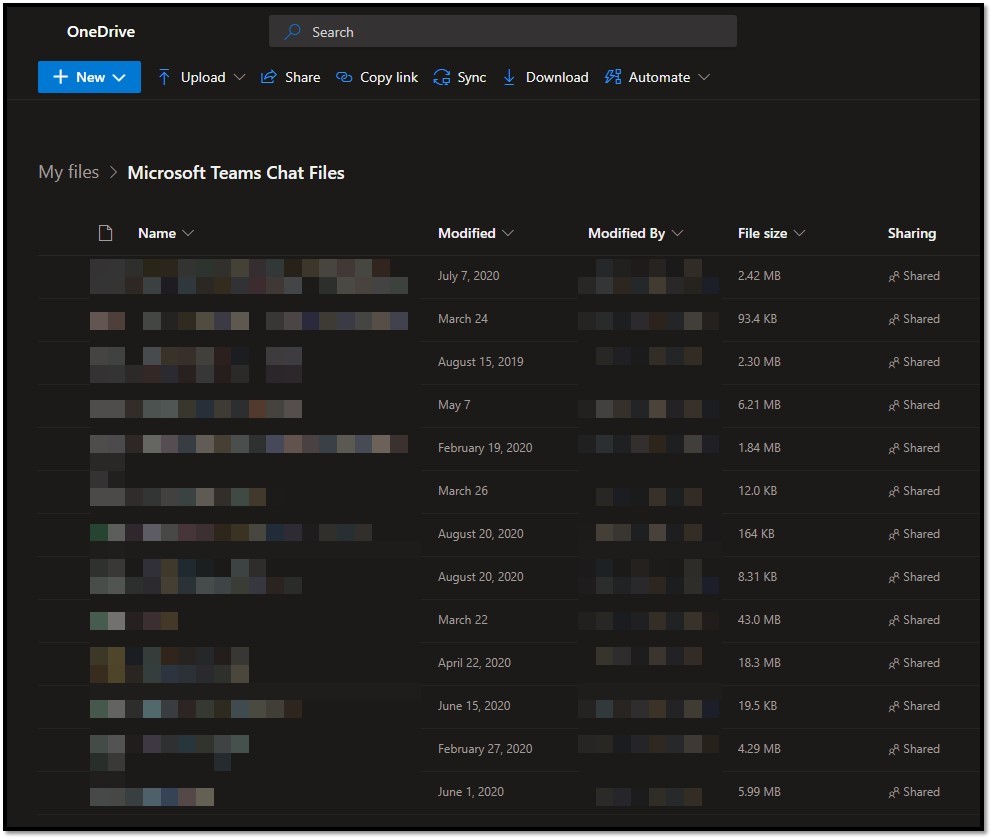
Managing & storing sensitive information in OneDrive
KCTCS promotes the use of OneDrive to help manage the viewing, editing, and distribution
of sensitive data elements. OneDrive is an authenticated file and data repository
that can be safely and securely accessed and linked to within the body of an email.
Simply upload the document containing sensitive data to OneDrive and share the secure
link to the document containing the sensitive information within the body of your
email. Using this approach, we can securely link to the sensitive data versus sharing
the data itself in the body of an email.
We will demonstrate how to securely share a link to your document containing sensitive
information in OneDrive below:
To start, go to your familiar MyPath web portal: https://kctcs.sharepoint.com/sites/mypath
Next, click on the OneDrive tile in your list of MyPath tilesets. This will take you to your KCTCS OneDrive directory:
 Next, go ahead create a folder that will house all your documents that contain sensitive
information. In the example below, we will be working with files that deal with Social
Security Numbers. We named the folder SensitiveData, which you would be able to see listed after you have created your new folder:
Next, go ahead create a folder that will house all your documents that contain sensitive
information. In the example below, we will be working with files that deal with Social
Security Numbers. We named the folder SensitiveData, which you would be able to see listed after you have created your new folder:
Any excel files you need to work with that contain sensitive information, just simply place them inside this folder. You can drag them off your desktop into this folder or create a new excel spreadsheet. Here is what this looks like:
If you need to share this with anyone, OneDrive makes this very simple and secure.
Just click here and choose who you’d like to share it with. It’s as simple as that
and keeps your data secure. Also, it prevents accidental viewing of sensitive information
to any unintended recipients!
In this particular example, we have shared this file with another user and this user
can only view the file.
If you wanted to allow the user to edit the document, select “Can Edit” instead:
They will receive an email with a link to the document you have shared with them after
hitting the SEND button:
Click Either the name of the document or the OPEN button to securely browse the document shared with you!
Encrypting sensitive information via Email:
If you are limited to work only within the body of an email and you are not able to
use Teams or OneDrive, we have presented another option below that is a secure means
of transmitting information.
We will be taking advantage of the “Encrypt” option for encrypting our email. This is available to click on using the Options tab of an email. When replying to a message using the preview pane, this will not
be visible. It is best to open the email in full without using the preview pane and
then navigate to the Options tab. It will be available to click when creating a new email. We will walk you through
how to Encrypt an email below:
1. Select Options at the top
2. Select Encrypt
3. Select Encrypt-Only
Sensitive Data Storage
All documents containing sensitive data should be stored appropriately to reduce the potential for disclosure. Documents should not be easily accessible to unauthorized individuals and any documents containing sensitive information should be placed with identifying information face down on counters and desks. These documents should not be left out on desks or countertops after business hours and should be placed in locked storage bins, locked desk drawers, or other secure areas.
PCI Compliance Standards and Procedures
To uphold PCI compliance standards and satisfy internal audit controls, KCTCS is required to enforce strict network security standards to prevent PCI cardholder data from traversing its primary network. This is typically accomplished using a dedicated circuit / isolated communication channel, such as a cellular service or DSL line.
Segregating cardholder data traffic from the main network minimizes the risk of data exposure, reduces the scope of compliance requirements, and mitigates the potential for lateral movement during a security breach. This approach aligns with PCI DSS Requirement 1, which mandates the implementation of robust network segmentation to isolate sensitive data.
By routing payment traffic through a separate, secure channel, KCTCS can ensure compliance while enhancing the integrity and confidentiality of cardholder information.
The recommended business procedure to satisfy PCI compliancy requirements can be found below:
- The college is responsible for working with the supplier/vendor to complete the purchase
of a dsl/cellular service for the vendor cardholder data to communicate through
- All Point of Sale devices are included in this scope by default
- KCTCS will assist in helping provide logical separation concerning the network topology/VLANS, Port security, etc
- KCTCS will perform a PCI compliancy scan after the setup has been completed to ensure all devices in scope are logically separate from the main network.
Sensitive Data Storage on Laptops
In cases where sensitive data is managed or stored on laptops, the information should be encrypted.
Sensitive Data Storage on Mobile Devices
All personal data on Apple iPhone is encrypted by default when a user creates an Apple ID and passcode. for instance, when your iPhone is locked with a passcode, Face ID, or Touch ID, encryption is in effect. Information is decrypted only when the device is unlocked. KCTCS asks that all devices be assigned a passcode, Face ID, or Touch ID to ensure the device's contents are secured from tampering. With those in place, information is decrypted only when the device is unlocked. It is also decrypted when shared using some applications or sometimes when stored in iCloud.
All modern Android phones are encrypted by default as long as you set up a lockscreen. In other words, simply set a pattern, PIN, or password to take advantage of Android's built-in encryption.
Sensitive Data Destruction
All media containing sensitive data including electronic, hardcopy, photocopy, etc., should be destroyed when it is no longer needed for business or legal reasons.
Electronic Media Destruction
Electronic storage media containing sensitive data including hard disks, portable drives, tape media, and CD/DVDs need to be rendered unrecoverable so that sensitive data cannot be reconstructed by secure wiping, degaussing, or physical destruction such as grinding or shredding hard disks.
Hardcopy Media Destruction
All hardcopy materials containing sensitive data that are generated in the course of copying, printing, or other sensitive information handling should be destroyed by shredding, incineration, or pulping processes so that sensitive data cannot be reconstructed.
Storage Media
Strict controls are in place to limit the accessibility of storage media containing sensitive data. All media containing sensitive data should be distributed in a secure manner both internally and externally. If it is necessary to remove computer-readable sensitive information from the secure area, the information must be protected with encryption.
All storage media containing sensitive data should be physically secured at all times.
KCTCS applies data disk encryption to ensure safe removal of hardware and electronic media to ensure sensitive data is secured going into and out of a facility, and the movement of these items within a facility.
If media is not inventoried, It is at risk for loss of identification in the event it is lost or stolen.
Displaying Sensitive Data
When the PAN is required to be displayed, it should be masked to only display the first six and last four digits of the PAN.
MDF/IDF Storage Security
All physical access to Data Center storage should be logged. The data center itself should always be locked and only permitted to authorized staff through the use of a keycard or other approved, comparable means of authentication. Data Center security is to be reviewed annually for managed providers. SOC reports are reviewed annually to ensure all physical and electronic KCTCS data is secured with the most current electronic and physical security protocols offered by the managed provider.
Transmission of Sensitive Data
Strong cryptography and security protocols should be used to safeguard sensitive data during transmission over open, public networks. Secure protocols such as SSL/TLS, IPSEC, SSH, etc. are the most effective means transmitting and safeguarding sensitive data.
End-user messaging technologies including e-mail, instant messaging, chat, etc. should never be used to send an unprotected primary account number (PAN).
Safeguards for Documents
All documents containing sensitive data are expected to be stored appropriately to reduce the potential for disclosure. Documents should not be easily accessible to unauthorized individuals and any documents containing sensitive information should be placed with identifying information face down on counters and desks. These documents should not be left out on desks or countertops after business hours and should be placed in locked storage bins, locked desk drawers, or other secure areas.
When discarding documents containing sensitive data, use a cross-cut shredder or place the document in a locked bin specifically designated as a shredding bin where the documents will be retrieved for shredding.
